ScriptRunner Blog
Getting Started with PowerShell Remoting
Table of Contents

PowerShell Remoting has been around since the early days of the PowerShell language and allows for running commands and receiving output between remote systems. Traditionally, PowerShell Remoting has been built on WinRM, but with newer PowerShell versions, the SSH protocol is now available to facilitate remoting between Linux systems as well. In this article, you’ll learn how to get started with PowerShell remoting, concentrating on PowerShell versions 5.1 and greater.
Requirements and Setup
PowerShell 5.1
- The Microsoft .NET Framework 4.5.2 or greater
- .NET 4.6.2 comes pre-installed on Windows Server 2016
- Windows Remote Management 5.1
- Ships in-box for Windows Server 2016 and greater
In this article we concentrate on Windows Server 2016 as prior versions have been deemed end-of-life by Microsoft.
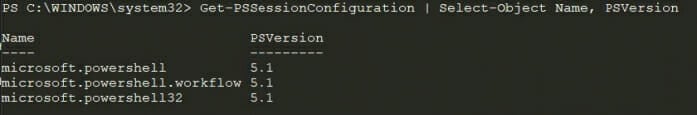
Take note that by default, Windows PowerShell will create a microsoft.powershell session endpoint. Enter-PSSession and New-PSSession will use this endpoint when no other session endpoint is specified. Since newer versions of PowerShell do not create or override this endpoint, the endpoint name must be specified to connect to the right remote instance, if not connecting to Windows PowerShell. An example of the default Windows PowerShell configuration is below (Figure 1).
PowerShell Core (6.x)
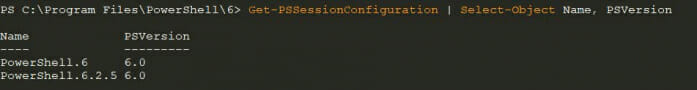
After running Enable-PSRemoting, the correct version-specific endpoints are registered, in this case 6.2.5 (figure 3).
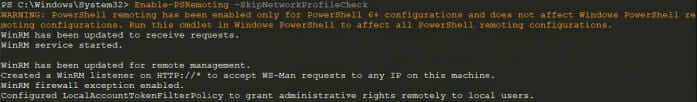
The reason that the -SkipNetworkProfileCheck parameter is specified is that any Public network will end the Enable-PSRemoting command early. As long as you are aware of the ramifications and proper control of this, then it is safe to run this command.
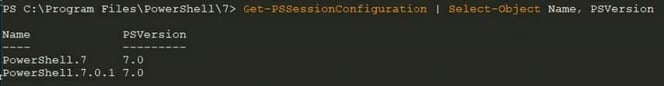
PowerShell 7
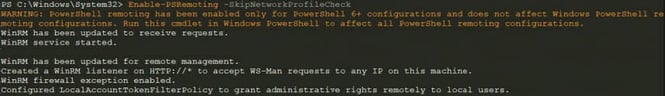
The endpoint names that are then registered to allow for remoting are specific to the latest PowerShell version, in this case 7.0.1. (see figure 5).
SSH Remoting Requirements
- PowerShell Core 6.x or PowerShell 7.x
- ssh.exe (client) and sshd.exe (server)
- Windows 10 build 1809 and Windows Server 2019 for built-in SSH (client)
Setup SSH Endpoints
- Install OpenSSH Server and Client
- OpenSSH for Windows is available directly in Windows 10 (1809 or higher) and Windows Server 2019 as an optional feature (visit Thomas Maurer’s Blog for instructions on how to install it on Windows 10 and on Windows Server)
- On Linux, you can install OpenSSH depending on your platform
- Configure the SSH subsystem to host a PowerShell process on the remote machine
Run the following commands to install the required capabilities (OpenSSH.Client may already be installed), service configuration, and firewall rules.
# Install the OpenSSH Client and Server Add-WindowsCapability -Online -Name 'OpenSSH.Client~~~~0.0.1.0' Add-WindowsCapability -Online -Name 'OpenSSH.Server~~~~0.0.1.0' # Initial Configuration of SSH Server Start-Service -Name 'sshd' Set-Service -Name 'sshd' -StartupType 'Automatic' # Confirm the Firewall rule is configured. It should be created automatically by setup. Get-NetFirewallRule -Name '*ssh*' | Format-Table -AutoSize # There should be a firewall rule named "OpenSSH-Server-In-TCP", which should be enabled New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
Finally, to enable the SSH server to work with PowerShell remoting, the subsystem must be correctly set.
notepad $Env:ProgramData\ssh\sshd_configWithin the sshd_config file, add the following configurations, specific to PowerShell 7. Once saved and configured, make sure to run the command Restart-Service -Name ‘sshd’ to restart the SSH server.
# Make sure that the subsystem line goes after the existing SFTP subsystem line Subsystem powershell c:/progra~1/powershell/7/pwsh.exe -sshs -NoLogo -NoProfile # Change c:/progra~1/powershell/7/pwsh.exe to c:/progra~1/powershell/6/pwsh.exe for PowerShell Core PasswordAuthentication yes # Below is optional but recommended to allow use of public/private keys PubkeyAuthentication yes
Finally, restart the SSH server:
Restart-Service -Name 'sshd'
There is a bug in the OpenSSH server version included with Windows. It requires that 8.3 short names be used for any file paths, hence c:/progra~1. To verify that you are using the correct 8.3 short name, you can use the following command to retrieve this for Program Files (where PowerShell 6 or 7 is installed):
Get-CimInstance Win32_Directory -Filter 'Name="C:\\Program Files"' | Select-Object EightDotThreeFileNameExample Commands for PowerShell Remoting
Gathering Information
$Params = @{
"ComputerName" = 'Host1'
"ConfigurationName" = 'PowerShell.7'
"ScriptBlock" = {
Get-Service | Where-Object Status -EQ 'Running' | Format-Table -AutoSize
}
}
Invoke-Command @Params
Running a Command
$Params = @{
"ComputerName" = 'Host1'
"ConfigurationName" = 'PowerShell.7'
"ScriptBlock" = {
Get-Service -Name 'Spooler' | Restart-Service
}
}
Invoke-Command @Params
Related posts
3 min read
ScriptRunner now available in the Microsoft Azure Marketplace
Apr 15, 2024 by Matthias Jütte
About the author:
Adam is a 20+ year veteran of IT and experienced online business professional. He’s an entrepreneur, IT influencer, Microsoft MVP, blogger, trainer, author and content marketing writer for multiple technology companies.