PowerShell is a powerful environment when it comes to querying information in Windows. PowerShell can be an important help, not only for scripts to edit server settings or workloads, but also for comprehensive information retrieval and report generation. In this article, we will show some PowerShell cmdlets that can gather extensive information from Active Directory (AD). Such query results are also interesting for troubleshooting. By the way, ScriptRunner has built-in queries, accomplishing the same but faster than scripted PowerShell queries - supplemented by your own scripted queries (using the function "with a script").
If the Active Directory Management module is installed in Windows 10/11 or Windows Server 2019/2022, you can also access specific Active Directory (AD) information in PowerShell. The Get-Command Get-Ad* command already shows numerous cmdlets that can display information from Active Directory.This also works smoothly over the network. The Get-Command -Module ActiveDirectory cmdlet displays all the cmdlets that can manage Active Directory. The command Get-Module -ListAvailable again shows all modules. This way, the names of the other modules can also be displayed and their cmdlets can be read out with Get-Command.
Display data from user accounts
The individual Get cmdlets can be extended with filters. For example, if you want to display all users that are not currently disabled, you may use:

Get user information from AD
To display the number of Active Directory users (AD users), you may use:
If you want to display the last logon of a user account, PowerShell is also available with different parameters:
The logon date of all user accounts can also be displayed as a list in PowerShell:
Locked user accounts can be displayed with Search-ADAccount -lockedout. Via PowerShell, the accounts can also be unlocked again, for example with Get-ADUser -Identity joost | Unlock-ADAccount
Display computer accounts in Active Directory
To also display the computer accounts from AD, additional cmdlets are available. With the pipeline, the result can be passed to "Select" and the data can be filtered for the desired information:
Like user accounts, you can count computer accounts in Active Directory:
Query domain controllers
When reading information from Active Directory, domain controllers in the environment play an important role. To view data about domain controllers, use the Get-ADDomaincontroller cmdlet. If you want to display information about all domain controllers in the environment, you can also filter the data, for example, with:
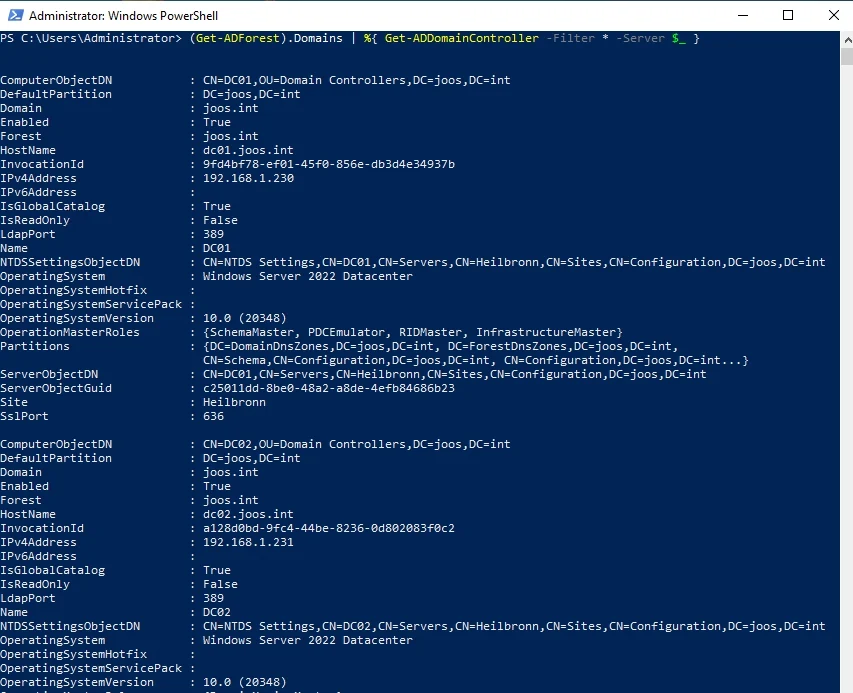
Displaying domain controller information in PowerShell
We'll touch upon more possibilities for this cmdlet later.
You can use the free Microsoft Active Directory Documentation Script to get an overview of what PowerShell scripts can do to extract information. You just need to run the script after extracting it. The script can also generate reports.
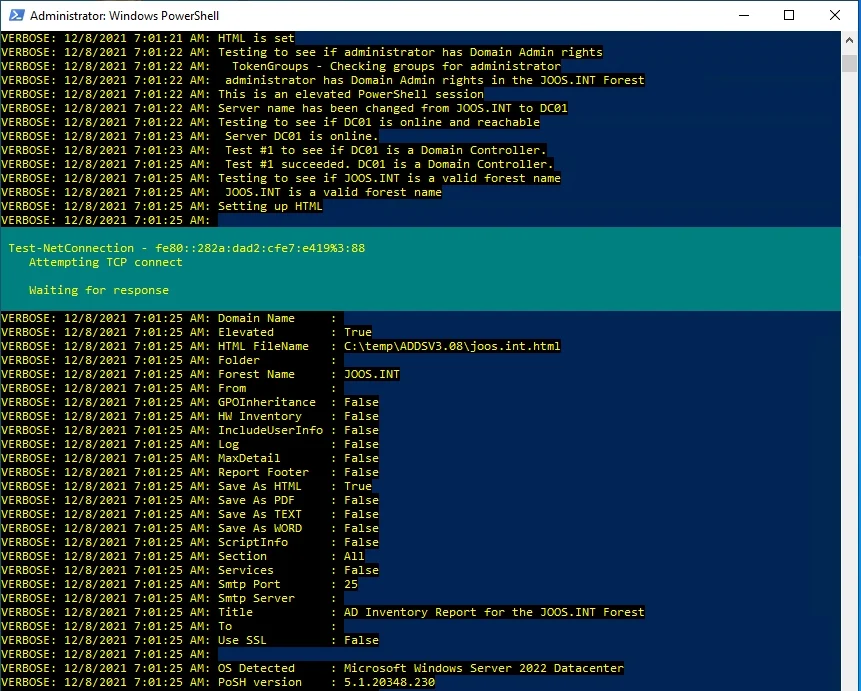
With a PowerShell script, you can also read extensive information from AD
Another script in this section is "ADinfo.ps1".
After starting, the script also displays information from Active Directory.
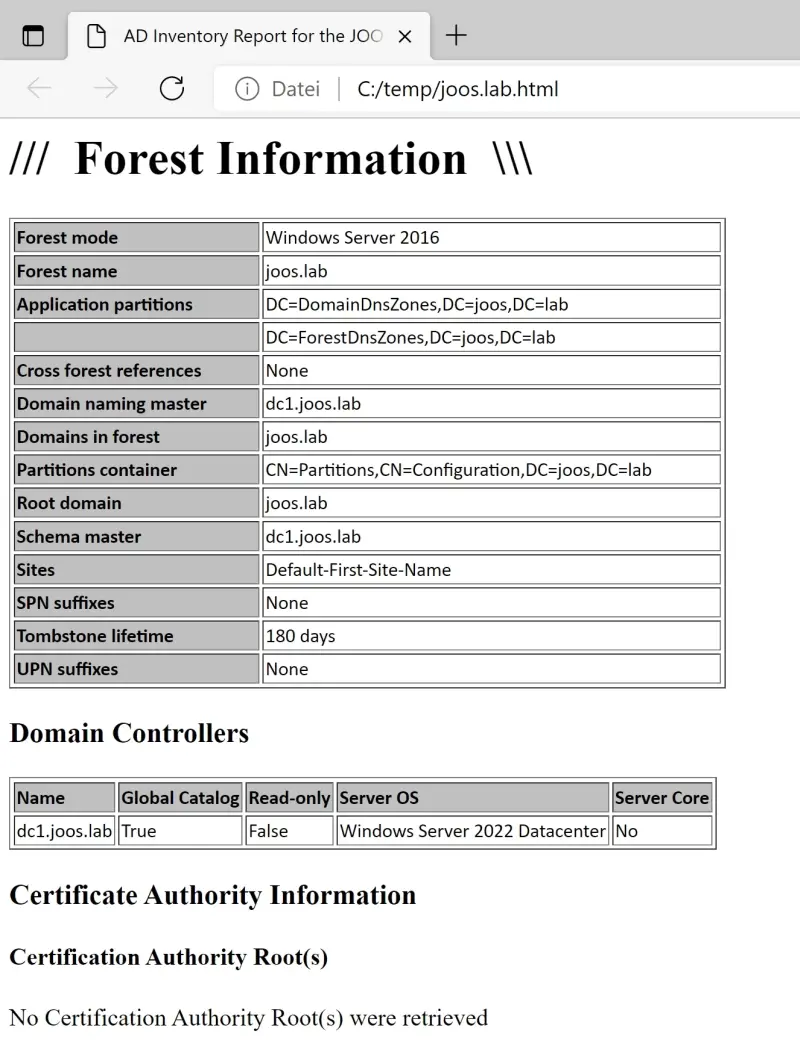
The output of information from PowerShell to HTML files is also no problem for PowerShell
However, PowerShell offers even more options. It is also possible to read out group policies, including the creation of reports. The command for this looks like this:
In PowerShell, you can also use Get-ADDefaultDomainPasswordPolicy to view the password policy settings in the domain. The settings are controlled in the Group Policy Management Console (gpmc.msc) for the corresponding policy. The path for password policy configuration is "Computer Configuration/Policies/Windows Settings/Security Settings/Account Policies/Password Policies".
Query DNS data and information on domains and overall structures
Active Directory and DNS work closely together. If there are problems in Active Directory, or if a documentation of the DNS zones is necessary, this can be done very easily with Get-DnsServerZone -ComputerName <DNS-Server>.The DNS records in Active Directory play an important role in allowing domain controllers to connect to each other. The check can also be done in the command line with "nslookup":
- Start "nslookup".
- Type "set type=all".
- Type "_ldap._tcp.dc._msdcs.<name of domain>", for example, "_ldap._tcp.dc._msdcs.joos.int".
In PowerShell, you can also use the various cmdlets to retrieve data from individual domains. The Get-ADDomain and Get-ADForest cmdlets display information about forest and domains. Pipes can be used to pass results from cmdlets to other cmdlets, for example, Get-ADDomainController. This is useful, for example, if you want to display the FSMO roles per domain. In each domain, there are the three FSMO roles that you display with the following command:
Schema master and domain name master exist only once per forest. This information can in turn be displayed with the CMDlet Get-ADForest:
Get-ADDomain initially displays the domain's operational masters (infrastructure, RID, and PDC), DNS name, domain controllers, operational mode, major organizational units, and other information.The Get-ADForest cmdlet additionally shows the domain name master, schema master, locations, UPN suffixes and domains. The two cmdlets provide all the relevant information about domains, structures, and forest in a few seconds. If you want to display the FSMO roles of a single domain controller, you may use:
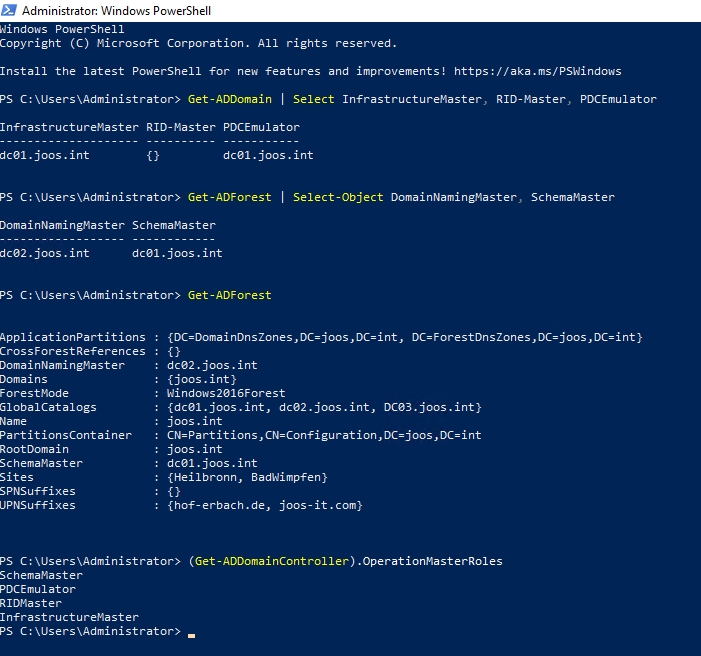
Viewing forest and domain information
In PowerShell, you can also view the domain controllers that have a specific role, for example, "PDC Master":
If you want to get a deeper look at domain controllers, use the Get-ADDomaincontroller cmdlet for domain controllers. Here, you can also see the IP address and FSMO roles that are active on the domain controller. In addition, you can also see which domain controllers are configured as global catalog and which operating system is installed on the server in which edition. The location to which the domain controller is assigned and which ports the server listens on in the network can also be found here.
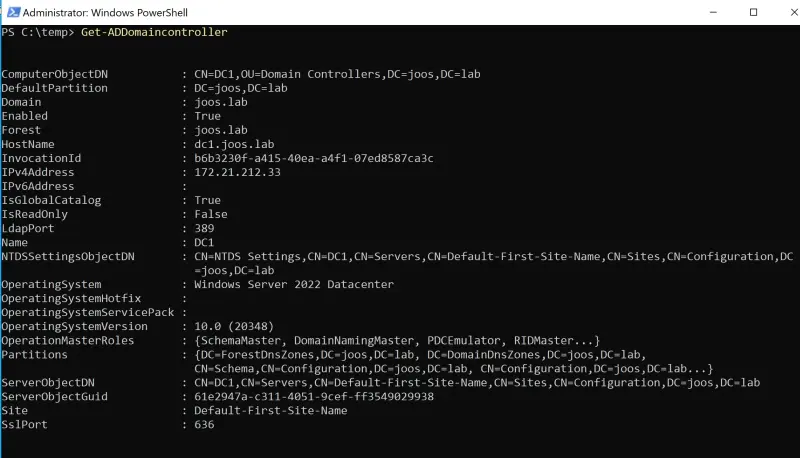
Querying information on domain controllers in Active Directory
Query and set deletion protection in PowerShell
Deletion protection in Active Directory prevents objects from being accidentally deleted. Whether the protection is active can be checked in the PowerShell. It is also possible to activate the protection for an object in this way:
The deletion protection can be activated with:
To go along with this topic, check out this ScriptRunner webinar:
Active Directory management Easy as that with PowerShell
Managing Active Directory users and groups is one of the central, recurring tasks of IT administration. In this webinar, we will show you how to standardize, automate and delegate these tasks in a time-saving way using PowerShell.
How to query Active Directory with ScriptRunner
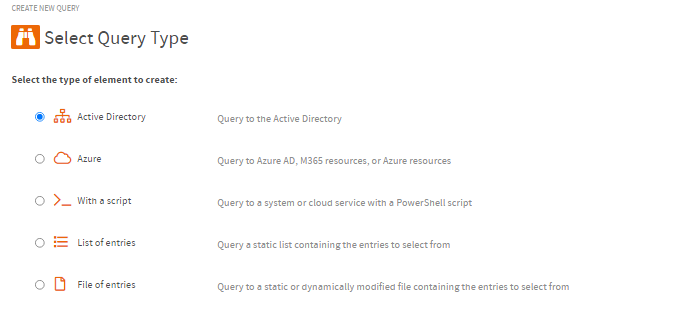
ScriptRunner already comes with different, ready to use types of queries. Common use cases are AD queries, which can be executed directly within the Windows domain.The appropriate queries are also available for Azure straight away. It is also possible to execute self-written scripts as queries by selecting the option "...with a script".With "List of Entries", predefined lists can be stored as selection, the last option "File of Entries" can be used to retrieve options in a file e.g. *.CSV.
Related links
- ScriptRunner ActionPacks will help you automate tasks
- Try out ScriptRunner here
- ScriptRunner: Book a demo with our product experts
.svg)
.svg)

