14 min read
Privacy Management with PowerShell – Let's look at the core features of Priva!
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.
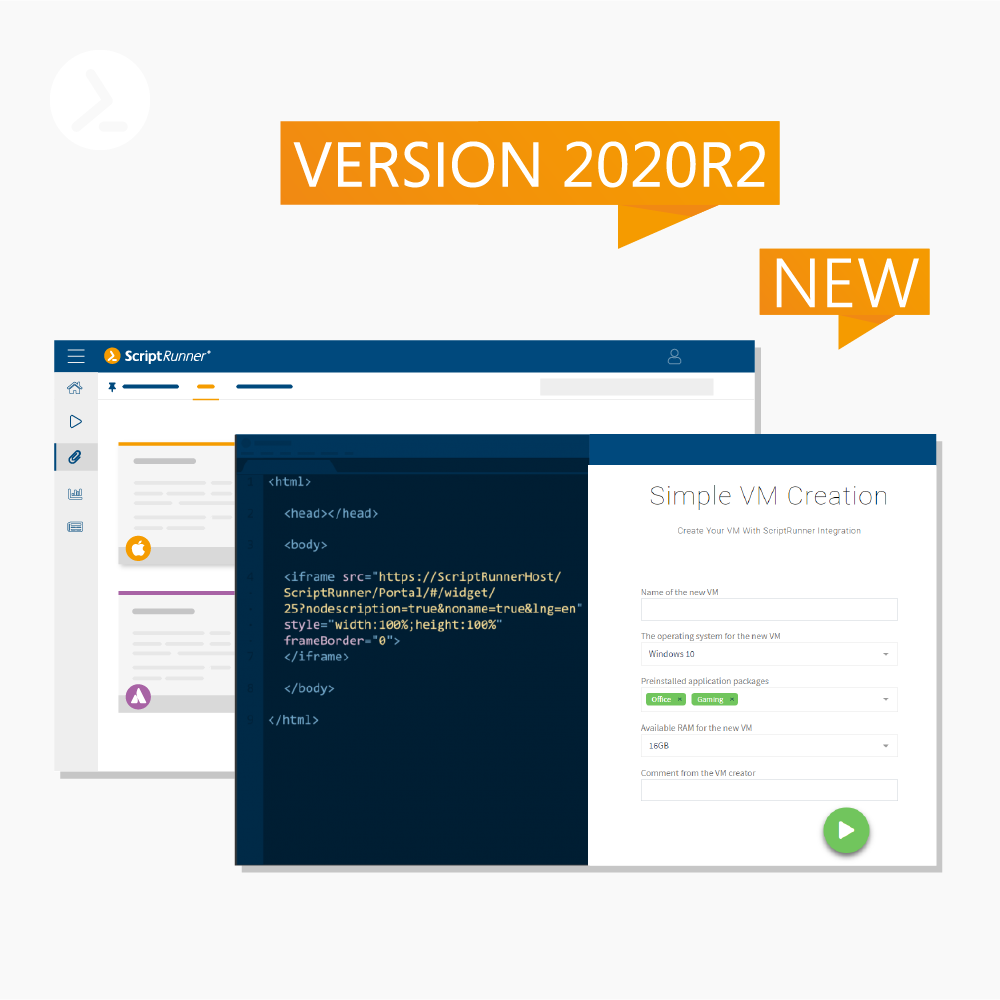
Version 2020R2 marks a new chapter in ScriptRunner’s integration with Azure AD, M365 Services, and Azure Cloud. At the same time, it is the first version to ship with the role-based portal, which will replace the previous web apps. Numerous additional features round off the 2020R2 release.
ScriptRunner is registered in Azure using app registration in Azure AD. This involves registering two apps, one for the ScriptRunner Service and one for the new ScriptRunner Portal.
The following functions are subsequently available with the ScriptRunner Service registration:
The registration creates the target system “Azure AD Home Tenant” in ScriptRunner.
Registering ScriptRunner Portal in Azure AD allows you to:
For more on ScriptRunner’s integration with Azure and registration, see the blog post ScriptRunner, Azure and M365 – a perfect trio and the ScriptRunner Settings Manual.
Important: after switching user login, you will no longer be able to log in users with their internal AD account. All configuration data in ScriptRunner Server and the web applications will be rewritten.
You can reverse the change by running the command
Unregister-AsrAzureADApp -TenantID -App Portal
on ScriptRunner Server.
For more on registration and login, see the ScriptRunner Settings Manual.

Fig. 1: The new Query Type Azure is now available for selection
To simplify usability for many use cases, the following options are available as templates:
The following can be used for customizable queries:
In the following, we will only consider the query for room selection. An Azure user query is used for this, which maps Exchange Online resources such as rooms as user objects. To control the query on room objects, a simple property filter on the Azure AD User Property DisplayName is used here.
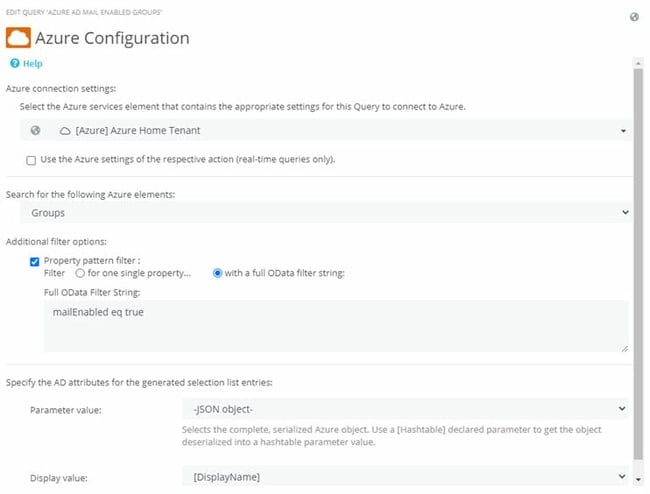
Figure 2: Querying objects whose DisplayName contains ‘room’
Testing the query is done as usual. If “-JSON-” was selected as the Value parameter in the query, the result set will contain a list of rooms as JSON objects. The value of the JSON object can be displayed via mouse-over. Further use of the JSON object is done with the new Feature PowerShell Splatting (see section “PowerShell Splatting feature”).
Note: Azure AD queries are case-sensitive!
Fig. 3: Filtering Azure AD groups with the ‘mailEnabled’ property
The Azure Group Query returns a list of all groups (with filters if necessary, as in Fig. 3). As parameter Value, the Object-Ids of the groups are required, since this ID variably controls the subsequent query to resolve the group into members (Fig. 4).
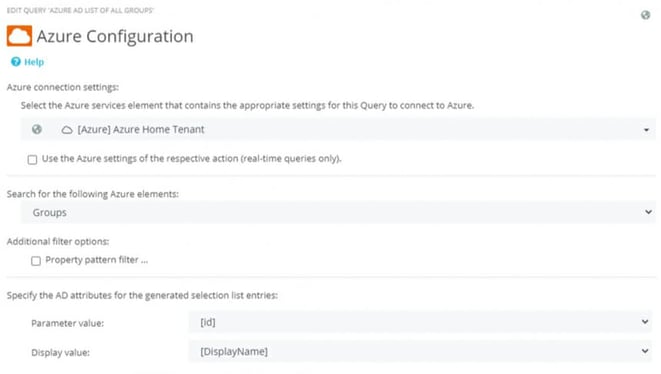
Fig. 4: Cascadable Azure Query where first a group is selected and then its members are listed as choices
The Azure Query to resolve the group returns a list of the group members along with the members’ property sets as a JSON object (Fig. 5)
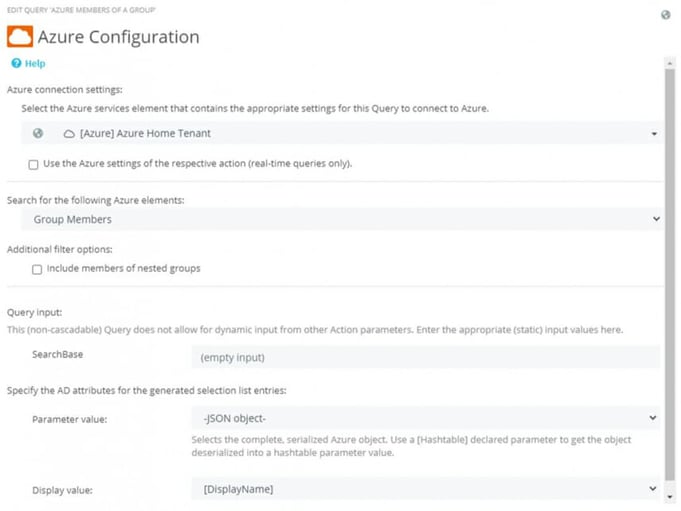
Fig. 5: The list of group members of their property sets are delivered as JSON object
The connection of both queries is done in the Action on the parameter page according to the already known scheme.
You can read more about Microsoft Graph and Azure resource queries in the blog post ScriptRunner, Azure and M365 – a perfect trio.
The portal replaces the ScriptRunner Delegate App and the ScriptRunner Self-Service App. Customers can install the new portal as part of the update to this release and switch users to the unified URL to access it.
The portal is divided into functional apps(Fig. 7) and supports logging in with Azure AD user accounts. If MFA is enabled, the second factor of authentication is also requested during login.
Fig. 7: Overview of the apps of the new ScriptRunner Portal in the Admin View
The entry into the portal as well as the available functions depend on the affiliation of a security group or an account to a ScriptRunner role.
Help desk and end users immediately start in the Run App. In addition, a help desk user has access to the Reports App.
Administrators have additional options in both of these apps. For example, the Action tiles can be directly customized in color and icon.
The new Statistics App (Fig. 8) makes it possible to make the benefits of ScriptRunner transparent.
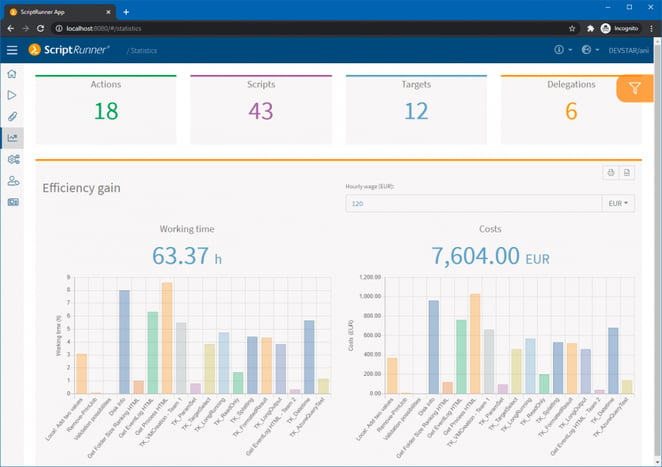
Fig. 8: The new Statistics App in ScriptRunner Portal
You can read more information and details about the new portal in the blog post The new role-based ScriptRunner Portal.
This allows “invisible” contextual use of ScriptRunner automated tasks in other applications. Thus, a ScriptRunner Action can be placed in the intranet for end users directly in the place that is related to it in terms of content (Fig. 9).
The widget can be used to expand the functionality of existing self-service portals, to add new functions to business applications and to upgrade ITSM systems.
Because it is so easy to integrate, there are no limits to what you can do, including customizing the styling.
Fig. 9: Application example of the ScriptRunner Portal Widget
Further information and details on the new Portal Widget can be found in the bog article The new role-based ScriptRunner Portal or on the Portal Widget page.
With the integration into Azure AD, enhancements and improvements in the role configuration have been implemented. For example, multiple groups and/or individual accounts can now be assigned to a role group in ScriptRunner.
To do this, simply click the + button at My Claims (Fig. 10). You can now add a group or an account.
Also a new feature is the search function for local groups/accounts, for Active Directory groups and accounts as well as Azure AD groups and accounts.
The Basic Auth option is reserved for use with Web Service Connectors.
Connection problems to target systems or cloud services are part of the everyday life of administrators. The causes can be manifold. The problems may stem from the infrastructure between ScriptRunner Server and the target system, such as firewalls, proxies, etc. Also, the target system may not be configured sufficiently (local firewall, remoting) or authentication fails.
Until now, test scripts had to be written and test Actions had to be set up. From this version on ScriptRunner takes over the connection test directly. This way, errors can be narrowed down and fixed faster. Simply select the target system, click on Test in the Action bar and then start test. The live output shows you what is happening.
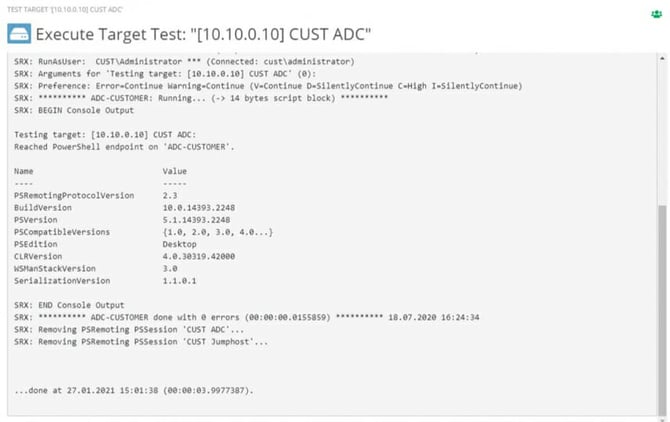
Fig. 11: Live output of a connection test
In the test run, a remote session is established with the stored credential to the target system and $PSVersion of the target system is returned. The connection is then closed again. The results can be viewed at any time as a PowerShell report.
The WinRM service in Windows offers the possibility to authenticate a PowerShell Remoting Session by means of a certificate. To do this, WinRM must be enabled over HTTPS on the target system and a certificate must be stored there. Details can be found in the Microsoft Documentation.
A corresponding credential is then configured in ScriptRunner. Next, you assign the credential to the target system and use the https option in the remoting settings.
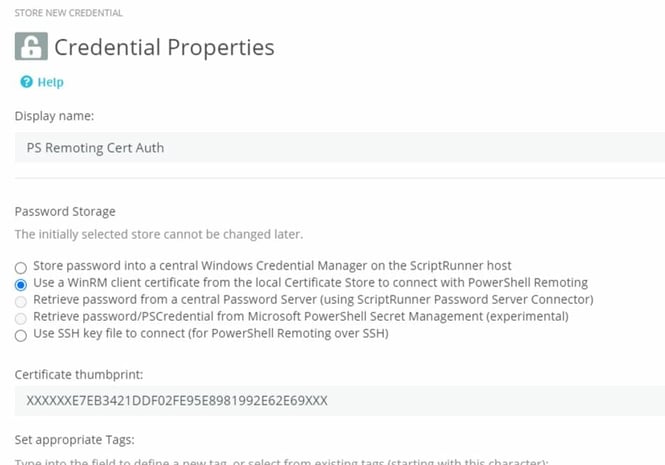
Fig. 12: ScriptRunner Credential for PowerShell Remoting with Certificate-based Authentication using WinRM
This new feature brings several advantages for the design of use cases in ScriptRunner. With a single query, multiple attributes or properties of an object can be determined and passed to the main script.
In this version, scripted queries and Azure queries can be used for this purpose. Thus, complex query cascades can be omitted, the use case becomes clearer for the user and several attributes can be processed more easily in a use case. The complexity in the PowerShell script is reduced because of the direct access to the content.
Scripted queries use a hashtable in the query script to which the results of the query are assigned. Using Azure Queries, the result set is stored in a JSON object.
Whether hashtable or JSON is used in the query, the results are passed encoded to a parameter in the main script to which the query was assigned.
The parameter in the main script must be of type hashtable. The structure of the hashtable follows the individual parameters to be used in the hashtable. The names of the parameters in the hashtable must match the names of the parameters in the query hashtable or JSON object. This will cause ScriptRunner to automatically map the matching values.
Additionally, a read-only attribute can be used for individual parameters of the hashtable. The following sample code shows the usage in the main Action script.
You can find further information on this feature in our Knowledge Base: Return multiple properties with a single Query.
The parameter attribute [Parameter(HelpMessage=”ASRDisplay(Splatting)”)] turns on the feature for the parameter [hashtable] $Address. This parameter $Address must be assigned the appropriate query in the Action configuration.
The other parameters in the hashtable itself define their structure. The parameter names must correspond to the names in the result set.
If an element is now selected from the result set in the UI (here “Peter Heim”), ScriptRunner automatically maps the values for the subsequent parameters.
With the parameter attribute [Parameter(HelpMessage=”ASRDisplay(Readonly)”)] the parameter [string] $Name is used in the UI as not changeable.
The [string] DateofBirth parameter is not given any values because it either does not exist in the result set or there is no name match for the parameter.
 Webinar Special
Webinar Special
Our latest ScriptRunner release 2020R2 comes with many new features. In this webinar we will cover the highlights of this version and how they help you with your automation journey.
Optimization of Queries with long runtime | ScriptRunner Knowledge Base
Return multiple properties with a single Query | ScriptRunner Knowledge Base
The new ScriptRunner portal – three becomes one | ScriptRunner
ScriptRunner, Azure and M365 – a perfect trio | ScriptRunner Blog
Security considerations for PowerShell Remoting using WinRM – PowerShell | Microsoft Docs
Jul 16, 2024 by Damian Scoles
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.
Jul 3, 2024 by Matthias Jütte
Every last Friday of July, we get to celebrate System Administrator Appreciation Day, a special day dedicated to...
Jul 2, 2024 by Philip Lorenz
Windows PowerShell 5.1 is usually preinstalled and the default – is it worth switching to PowerShell 7, or will it lead...
Frank Kresse is Head of Product and CEO of ScriptRunner. As the inventor of the automation and delegation solution for PowerShell, he advises clients on use case scenarios and develops solutions for the automation and the digitalization of their processes. He is also involved in technology start-ups.