14 min read
Privacy Management with PowerShell – Let's look at the core features of Priva!
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.

Authentication via credentials is the most common form of access identification in PowerShell.
This is done using the Credential parameter, to which the combination of user name and password is passed in the form of a PSCredential object. Since these are sensitive data from privileged accounts, the security of these accounts must enjoy the highest priority. However, the most common methods of dealing with credentials have significant security gaps, as shown below.
The easiest way to create a PSCredential object is a code like this:
$user = "Max_Mustermann" $pwd = "Passwort123" $secure_pwd = $password | ConvertTo-SecureString -AsPlainText -Force $creds = New-Object System.Management.Automation.PSCredential -ArgumentList $user, $secure_pwd
The username and password are entered as plain text in the PowerShell script. The password is converted to a SecureString because it can only be passed in this form. The PSCredential object is then created. This approach is extremely critical from a safety point of view. The username and password are entered as plain text in the script and are therefore visible to everyone.
The following code offers more security:
$user = "Max_Mustermann" $secure_pwd = Read-Host -AsSecureString $cred = New-Object System.Management.Automation.PSCredential -ArgumentList $user, $secure_pwd
Only the user name is entered as plain text in the PowerShell script, the password is created directly as SecureString. However, there are security holes in this method as well, since you can make a reference to the username in the script. In addition, neither automation nor delegation of scripts is possible, since the password must be entered interactively each time a new script is executed.
The password can also be stored in an external file:
Read-Host -AsSecureString | ConvertFrom-SecureString | Out-File "C:passwort.txt" $user = "Max_Mustermann" $pwd = "C:Password.txt" $cred = New-Object -TypeName System.Management.Automation.PSCredential $User, (Get-Content $pwd | ConvertTo-SecureString)
With this method, the password is encrypted and stored in an external text file. This is read back into the script and converted into a SecureString. This allows scripts to be automated since user names and passwords no longer have to be entered interactively. However, this procedure is not completely secure either, as SecureStrings can also be converted back in order to obtain the password. Another disadvantage is that the text file must be accessible during execution, which makes it impossible to delegate scripts. The user name is also entered as plain text in the script here.
One very popular way to create a PSCredential object is to use the Get-Credential cmdlet:
$cred = Get-Credential -Message "Bitte geben Sie Nutzername und Passwort ein"
That way, the user can use an input box to enter the username and password (Figure 1). The entered password is stored as SecureString.
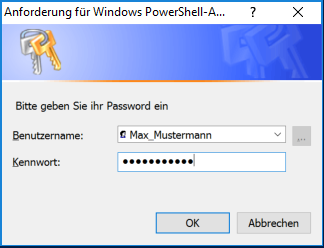
Fig. 1: Dialog box for entering username and password, based on a PSCredential object
Although this method has no security vulnerabilities, it must be entered interactively in the PowerShell Console each time the script is run. This prevents both automation and delegation of scripts.
ScriptRunner allows you to safely store credentials and fully automate your scripts. Under the menu item “User Accounts” all Privileged Accounts with password are stored, which ScriptRunner should use to execute scripts on other systems. Passwords and usernames are stored in the Windows Credential Manager on the local system of the ScriptRunner host. The username is replaced by a randomly generated number as an additional security precaution. Since the information is stored on the local system, a normal Windows user cannot access it.
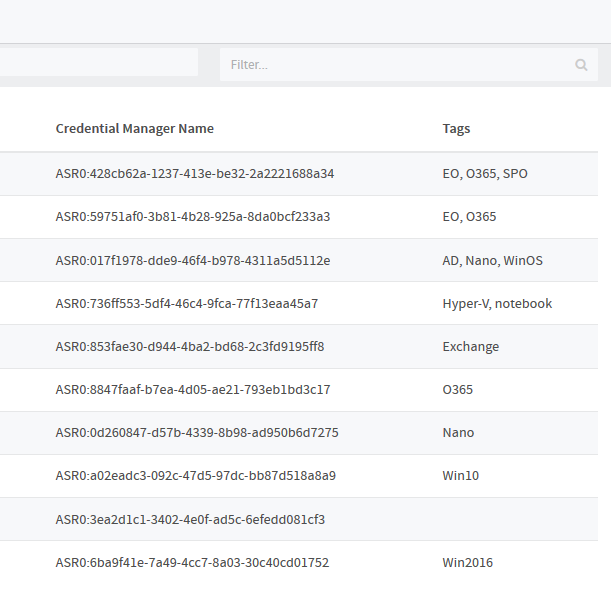
Figure 2: All privileged accounts and passwords that ScriptRunner needs to use to run scripts on other systems are stored locally on the ScriptRunner host
In the PowerShell script, the required credentials are simply inserted as variables, without any reference to the username or password used in the script.
Param ( [PSCredential] $PSCred1, [PSCredential] $PSCred1 )
Actions are always started from the ScriptRunner host with the credentials stored there. The required credentials are configured in the action/policy and are only introduced into the PowerShell process at runtime.
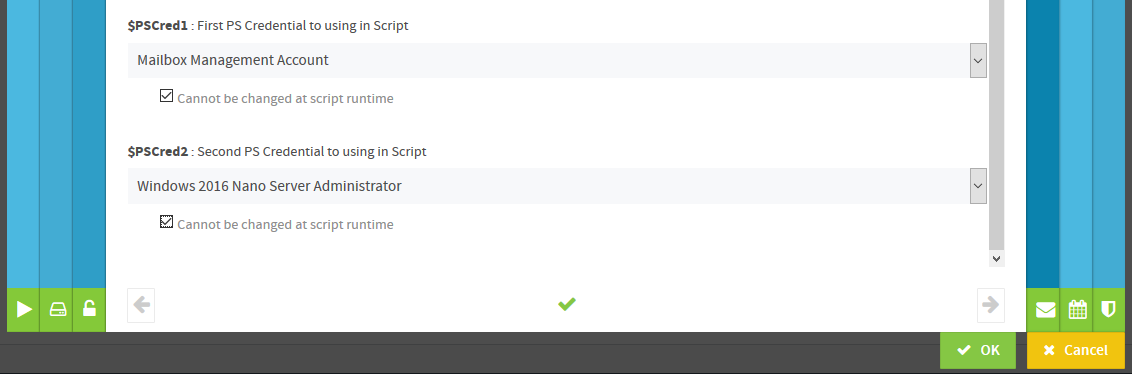
Since there is no interactive input of the username and password at runtime, Service Desk users of delegated scripts do not need to know the name or password of an administrative account to perform an action.
Download the free PowerShell Security-Guide and learn about
And many more topics!
Jul 16, 2024 by Damian Scoles
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.
Jul 3, 2024 by Matthias Jütte
Every last Friday of July, we get to celebrate System Administrator Appreciation Day, a special day dedicated to...
Jul 2, 2024 by Philip Lorenz
Windows PowerShell 5.1 is usually preinstalled and the default – is it worth switching to PowerShell 7, or will it lead...
Frank Kresse is Head of Product and CEO of ScriptRunner. As the inventor of the automation and delegation solution for PowerShell, he advises clients on use case scenarios and develops solutions for the automation and the digitalization of their processes. He is also involved in technology start-ups.