14 min read
Privacy Management with PowerShell – Let's look at the core features of Priva!
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.
ScriptRunner is the central hub for PowerShell and communicates with its users, the target systems as well as with third party systems. Several aspects are important for communication:
In this blog article you get to know the shell model and learn which security concept ScriptRunner is based on and how the communication relationships of ScriptRunner look like in a typical customer environment.
Before we deal in detail with the individual communication protocols and partners, it is worth taking a look at the basic security concept, which ScriptRunner depicts. The starting point is a shell model. In contrast to conventional views of network sections, firewalls and VPNs, the shell model offers the advantage of defining security levels and thus zones independently of the concrete infrastructure.
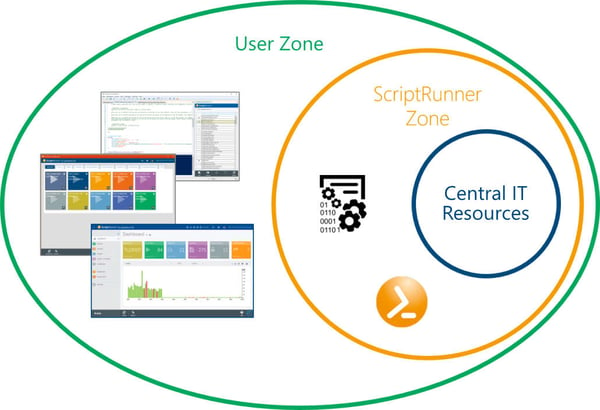
The ScriptRunner shell model with three security zones
Three security levels are defined in the figure:
The core principle in this model is that communication between two partners may only take place across a shell boundary. Access from the user zone to the inner zone is not permitted.
This means that communication can only take place between actors in neighboring shells.
This results in the following permitted communication relationships:
As a consequence, there are significant advantages for the entire IT security because only this model enables an effective separation of rights and access. A help desk employee only has access to the actions assigned to him with his user account. Only the ScriptRunner host has the necessary rights to execute the script of the action on the target system. The user is completely decoupled from this and therefore requires no knowledge of the administrative rights for the target systems. The same applies to calling systems such as monitoring, ITSM and workflows.
The concept of security shells can be extended by further shells, e.g. for administrative access via the Internet or from Internet-based monitoring or ITSM systems to ScriptRunner.
In a typical customer environment, different actors are involved in the communication with ScriptRunner. The communication partners are distributed over the three levels mentioned above:
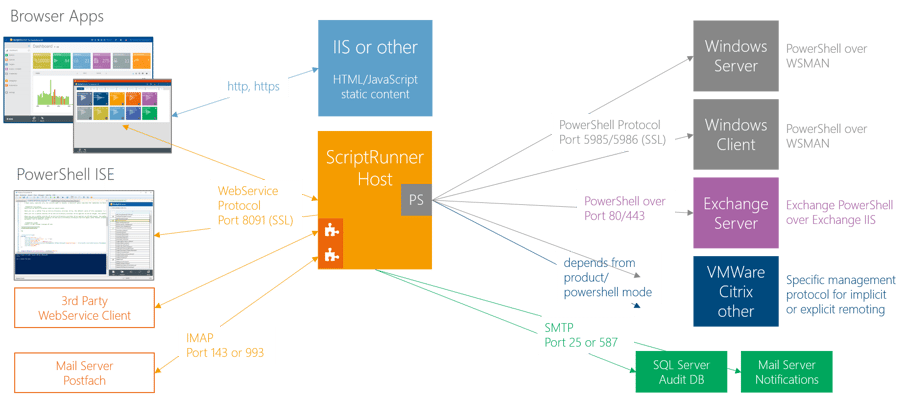
The ScriptRunner communication relationships
At this level, users as well as various third party systems call functions in ScriptRunner:
At the ScriptRunner level two central components of ScriptRunner are shown:
At the execution level, there are typically the various target systems on which PowerShell scripts are to be executed in a controlled manner, for example:
From ScriptRunner’s point of view, there are optionally two further systems on this level:
The following example shall illustrate the entire process. A user starts the Delegate App and performs an Action in his role context.
The web browser contacts the IIS to call up the Delegate App and requests the website content.
The IIS web server returns the requested content in HTML, JavaScript and CSS format to the browser. Communication takes place via the standardized transmission protocols HTTP and HTTPS, usually via port 80 (HTTP) and port 443 (HTTPS).
The JavaScript application then starts in the browser and contacts the ScriptRunner host via the web service interface. The client uses the web service protocol ODATA/REST on the standard port 8091 for this purpose. If the authentication was successful, the data is loaded into the application. The Delegate App displays the tiles assigned to the user or group.
Now the user can select an Action, fill in the necessary entries and start the action. All execution policies, target systems, connectors, administrative accounts, roles and settings are organized in the central ScriptRunner repository. The host now starts an isolated PowerShell process in the script policy with all necessary data and information, contacts the target system and sends it the job “Execute this script”. After the scripts in the PowerShell have been executed on the target system, the result data is sent back to the ScriptRunner host.
The ScriptRunner Service then checks the result. If it is correct, it is forwarded to the application and the user is informed about the successful execution or, alternatively, an error.
The communication between ScriptRunner Service and target system depends primarily on the target system. This can be done using the standard PowerShell protocol (ports 5985 and 5986), http/https (Exchange), or management protocols from products from various vendors. In this case, the protocol conversion takes place in the PowerShell module of the respective product.
For an error-free operation it is very important to understand the communication and the process of the specific target system and to adapt the configuration in ScriptRunner accordingly.

Jul 16, 2024 by Damian Scoles
All you need to know about Privacy Management, privacy management policies, rules, and subject rights requests.
Jul 3, 2024 by Matthias Jütte
Every last Friday of July, we get to celebrate System Administrator Appreciation Day, a special day dedicated to...
Jul 2, 2024 by Philip Lorenz
Windows PowerShell 5.1 is usually preinstalled and the default – is it worth switching to PowerShell 7, or will it lead...
Frank Kresse is Head of Product and CEO of ScriptRunner. As the inventor of the automation and delegation solution for PowerShell, he advises clients on use case scenarios and develops solutions for the automation and the digitalization of their processes. He is also involved in technology start-ups.